Imagicle for Microsoft Teams Webinar Series
Getting started with OWASP Web Security Test Guide.
- allow you to test only the exposed code;
- are performed at the end of the SDLC, so they are easily integrated into our Continuous Integration system.
Designing a Secure Software Development Life Cycle.
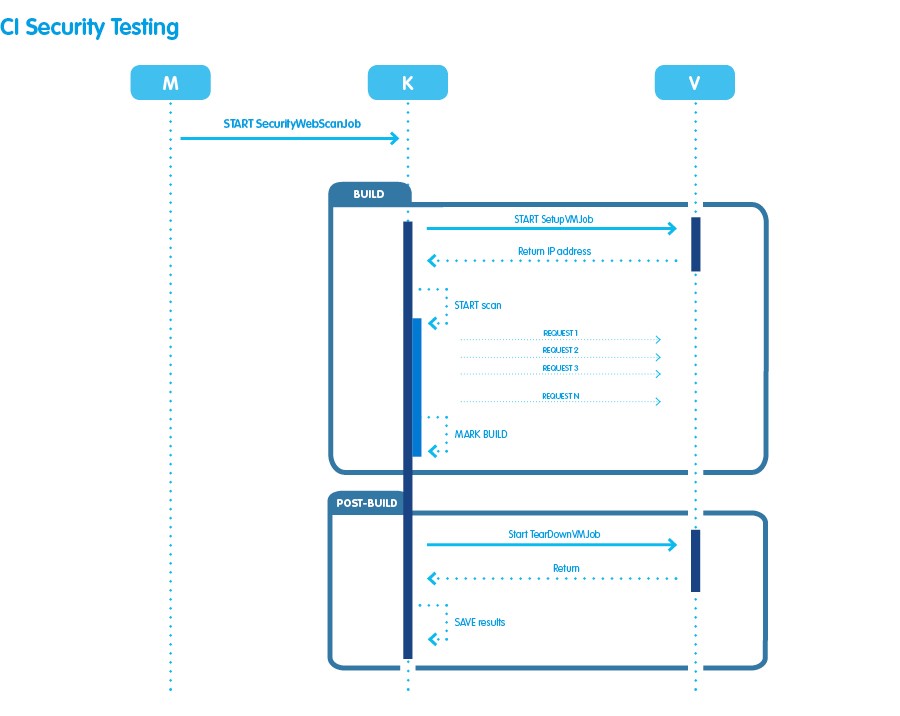
- M: Jenkins’ master node;
- K: a new machine on which we have installed our web scanner and will be our slave node where the job that governs the scan will be performed;
- V: another Jenkins slave node where the setup and teardown jobs that will be discussed later will be performed.
- the previously prepared snapshot is restored;
- all Windows Updates are made with the necessary restarts;
- the installation of the latest package created by the master branch of our repository is launched;
- once the installation is successfully completed, the setup job communicates the IP address of the web portal.
- a first phase of “discovery” of the web pages;
- a second phase in which the pages found are tested to check for any vulnerabilities.
- SUCCESS, if no vulnerabilities of the configured severity and confidence have been detected;
- FAILURE, if vulnerabilities have been detected.
- duplication of tests performed is avoided;
- the application is tested for a greater number of vulnerabilities;
- a test standard is created, regardless of the user’s ability.
Conclusions.
#stayimagicle
You might also be interested in…
-
Download
Security BlogStay Compliant: A Complete Guide to Compliance Recording.
Stay Compliant: A Complete Guide to Compliance Recording.Learn how to navigate regulatory requirements, protect sensitive information, and optimize your recording processes. -
Use Case Blog
Why Recording Call and Contact Center Calls Is Essential
Why Recording Call and Contact Center Calls Is EssentialUnlock insights and elevate customer service with advanced call recording and analytics from Imagicle. -
Products Blog
Voice Analytics: designed for your privacy and security.
Voice Analytics: designed for your privacy and security.Voice Analytics handles a variety of sensitive, personal data. Learn why you can trust it to do so, any time, anywhere.
Security Blog
Stay Compliant: A Complete Guide to Compliance Recording.
Stay Compliant: A Complete Guide to Compliance Recording.
Learn how to navigate regulatory requirements, protect sensitive information, and optimize your recording processes.
Use Case Blog
Why Recording Call and Contact Center Calls Is Essential
Why Recording Call and Contact Center Calls Is Essential
Unlock insights and elevate customer service with advanced call recording and analytics from Imagicle.
Products Blog
Voice Analytics: designed for your privacy and security.
Voice Analytics: designed for your privacy and security.
Voice Analytics handles a variety of sensitive, personal data. Learn why you can trust it to do so, any time, anywhere. Welcome
Welcome Automate
Automate Ensure
Ensure Analyze
Analyze Other
Other

0 Comments